Cybercrime is on the rise.
A report from Accenture revealed that there has been a 67% increase in security breaches over the past five years. And it is not just the number of attacks that is growing; so, too, is the sophistication of the cybercriminals targeting organizations around the world.
Businesses in all industries are affected, but some of the most vulnerable to attack are e-commerce sites.
If your e-commerce business has not yet suffered a cyber attack, you should consider yourself one of the lucky ones (although, as any cyber-professional would say: not for long). It is essential that you do everything you can to mitigate the risk of a breach by putting robust defenses in place before a security attack.

In this article, we'll take a look at how you can keep your e-commerce site secure.
Why Cybercriminals Are Targeting E-commerce Sites
One of the key reasons that cybercriminals focus on e-commerce sites is simply because, unfortunately, they are attractive targets.
Gaining access to the systems of an e-commerce site can provide criminals with a range of valuable data. And not just money, but also customers' personal and financial details, which can be lucrative to criminals by committing identify fraud or selling the data on the dark web.
The darknet [or dark web] is a network, built on top of the Internet, that is purposefully hidden, meaning it has been designed specifically for anonymity. Unlike the deep web, the darknet is only accessible with special tools and software – browsers and other protocol beyond direct links or credentials. You cannot access the darknet by simply typing a dark web address into your web browser.
In addition, e-commerce sites are hacked more often because they are seen as easier targets, as there is a growing number of webmasters who do not regularly patch their underlying CMS systems. E-commerce sites that run on CMS systems like Magento, Joomla and OpenCart are more likely to be successfully hacked when they run an out-of-date version of the platform:
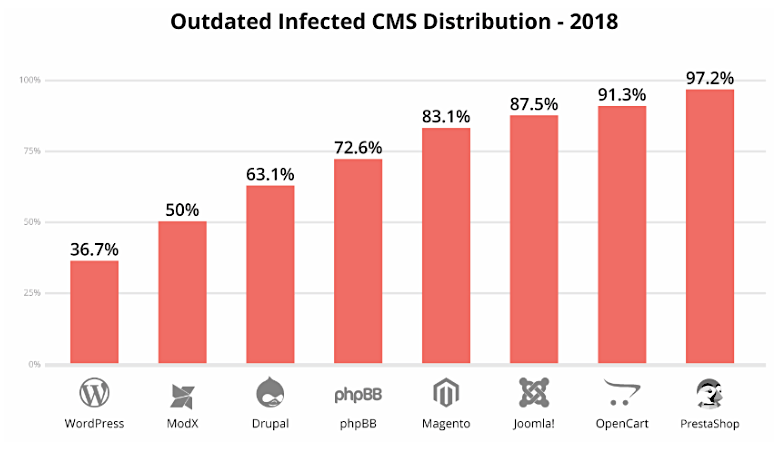
Many websites also have web applications and these can contain vulnerabilities that attackers can exploit.
Related Content: 5 E-commerce Trends You Can’t Ignore in 2020
Why Are E-commerce Sites More Vulnerable?
It's easy for businesses (especially e-commerce) to get into the habit of prioritizing website functionality over cybersecurity, and this can unknowingly leave them at risk. But this is far from the only reason that e-commerce websites are vulnerable to various types of cyber attacks.
Here are a few other reasons why e-commerce sites are more vulnerable:
- Some e-commerce business are relatively small operations with few members of staff and relatively low operating costs.
- SMBs that are less able to spend significant amounts of money on cybersecurity are naturally more vulnerable to attacks. Without the budget to spend heavily on improving defenses, sites can be more easily compromised by cybercriminals.
- E-commerce businesses are often entirely reliant on their website, which means that if the site is hacked and has to be taken offline or if key data is lost, it can seriously impact the ability of the business to continue operating.
And there are other issues at play here, too, including the impact of industry problems such as a cyber skills shortage. It has been predicted that there will be 1.8 million unfilled cybersecurity positions by 2022 – indicating that even those businesses that are willing to put in the investment necessary to keep themselves secure may find it difficult to employ the needed staff.
Dive Deeper: How Poor Website Security Negatively Impacts SEO Rankings
Why You Need to Protect Your Site
Cybersecurity is an issue for businesses of all sizes and across all industries, and it is not something that any organization can afford to ignore anymore. If you run an e-commerce site, website security plays a much larger role than just keeping your own private information secure – it has the potential to affect almost every aspect of your business.
Firstly, if you are the victim of a cyber attack, it can be a huge issue for your future customer confidence:
- 87% of customers say that they will take their business elsewhere if they do not trust a company to handle their data responsibly.
- 88% say that the amount of data they share with a company depends on how much they trust it
- 92% say that companies must be proactive about data protection

This is massive issue – suffering a cyber attack could not only lose you immediate business and money, but also affect your ability to retain or attract new customers. Perhaps it is not surprising, then, to learn that 60% of small companies go out of business within six months of suffering a cyber attack.
And it is not just customer confidence that can take a hit when a site is attacked – it can also affect shareholder and investor confidence. If your business utilizes financial backing from elsewhere, this can be seriously endangered by suffering a data breach.
Worse, the attack can have knock-on effects across many areas of the business that you might not even realize, such as disrupting your operations and reducing the availability of your services. It can even compromise your SEO efforts by causing Google blacklisting or having the content of your pages altered.
The effects linger too. You might even find that well after the cyber attack is over, you are still struggling with the aftermath. If your e-commerce site has not followed important regulations such as the General Data Protection Regulation (GDPR) and subsequently suffered a cyber attack, you could face severe penalties.
This is also true of Payment Card Industry Data Security Standard (PCI DSS) – the rules that businesses processing card payments need to comply with. All e-commerce sites process card payments, so it is absolutely essential that proper controls are put in place to keep your business compliant.
Dive Deeper: The Email Marketer’s 4-Step Guide to GDPR Compliance
Common Tactics Used in a Cyber Attack
There are many different tactics and techniques, and the best way to be prepared is to understand how they are used by cybercriminals.
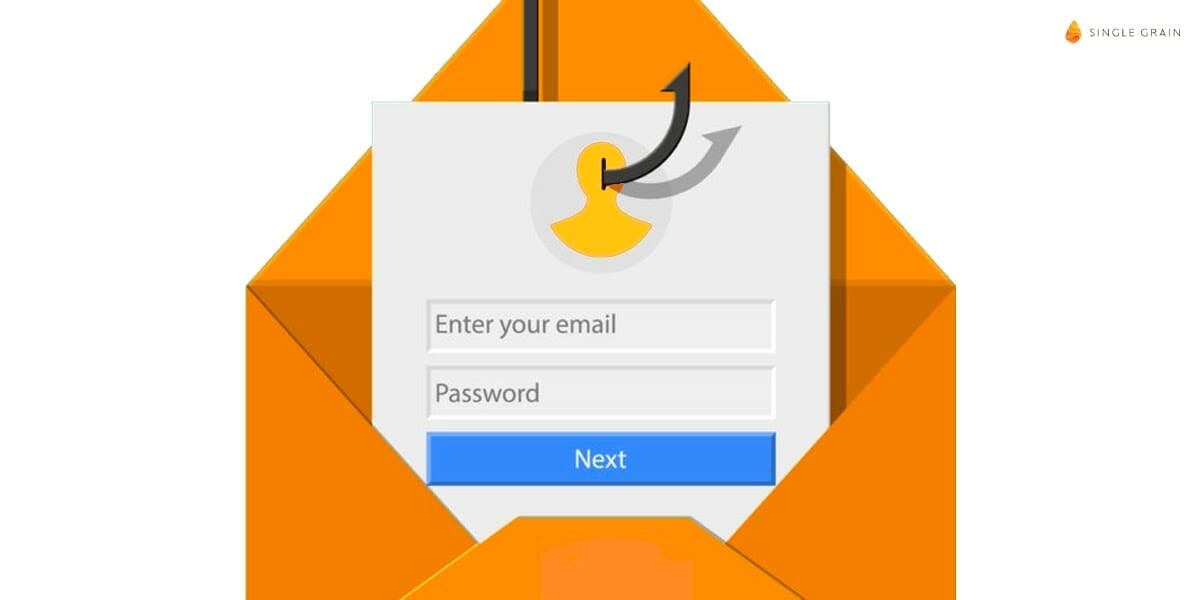
Phishing
Phishing is one of the most common forms of cybercrime – and it something that many people are aware of, even if they do not know it by name.
Phishing can take many forms, but it is often the practice of a cybercriminal attempting to gain a password or other personal information by pretending to be a reputable source:

It may involve the criminal sending an email to a web admin or member of staff; this email pretends to be from a legitimate source such as a partner company, email or web services provider, or even an internal CMS.
These deceptive emails are designed to look exactly like a genuine email sent from a legitimate company, and often ask individuals to click a link where they are sent to a fake version of a familiar site, so that criminals can gain usernames and passwords.
Social Engineering
In cybersecurity terms, social engineering refers to the practice of manipulating members of staff in order to make them give up information. As per CSO:
Social engineering is the art of exploiting human psychology, rather than technical hacking techniques, to gain access to buildings, systems or data.
Once again, social engineering can take many forms, and it could be something as simple as someone calling your business claiming to be a customer who needs to make changes to an order.
Alternatively, the criminal could claim to be from a legitimate service such as Microsoft, and stress the need to authenticate or deal with a problem. The ultimate goal is for the criminal to be able to gain access to data, information or passwords without the individual realizing that any crime has taken place.
If you think you're too smart or too seasoned to fall for these scams, read Five Social Engineering Tricks and Tactics Employees Still Fall For.
Dive Deeper: 6 Tips for Securing Your Data from Cyber Attacks as a Remote Worker
Insider Threats
E-commerce businesses also need to be aware of the dangers of insider attacks. This is an increasing problem across cybersecurity: Verizon's 2019 Data Breach Investigations Report revealed that 34% of breaches were caused by insiders.
No one wants to believe that their staff would act maliciously against them, but it does happen and businesses need to be aware of it. This can come from disgruntled former employees or even current employees (those with access to your system) who see the opportunity to profit from criminal activity.
Code Injection
It is also a common issue that criminal hackers will target your e-commerce site through vulnerabilities in the programs you use. One of the ways that they can achieve this is through SQL injection:
An SQL injection is a code injection technique and a nefarious negative SEO technique that a criminal hacker may deploy to bring down your site. The attacker gains access to the backend of your database by injecting codes into vulnerable or corrupt database content via web page input (such as a user inputting their “username” with an SQL statement). It is still one of the most common threats because it is highly effective.
This code injection involves malicious commands being executed in order to take information from backend databases, which can be a way for criminal hackers to gain a lot of personal information and credit card details whilst being very difficult to identify.
Software Subversion
E-commerce sites are also specifically vulnerable to software subversion, where they can be targeted through their supply chain. This occurs when cyber criminals compromise software and plugins that are widely used.
One of the most well-known is the Magecart attack which managed to compromise a script in ads shown on e-commerce sites and was able to target hundreds of sites simultaneously:
MageCart infections are when attackers compromise an e-commerce site to inject JavaScript into the checkout or cart pages. This script then steals credit card and address information entered into these pages and then sends it off to a remote server for the attackers to collect.
DDoS Attack
DDoS attacks are another major issue:
A distributed denial of service (DDoS) attack is when an attacker, or attackers, attempt to make it impossible for a service to be delivered. This can be achieved by thwarting access to virtually anything: servers, devices, services, networks, applications, and even specific transactions within applications.
They are designed to cause disruption – from the minor inconvenience of a disrupted service to entire websites or businesses crashing – and often timed to coincide with busy shopping periods, making them very difficult to detect.

Tips to Keep Your E-commerce Site Secure
There are actually many things that your business can do to keep your operation secure against these cyber threats. While some might sound complicated or technical, they are things that your webmaster should be able to leverage to defend your organization more effectively against cybercrime. Some practical steps include:
Monitor Systems and Assets
If you aren't already, start monitoring your web servers, either manually by an administrator or by using automated software such as SIEM (Security Information and Event Management). When servers, logs and web traffic are monitored, it can help you identify any suspicious behaviors or unusual activity before it turns into a full-blown cyber attack.
These suspicious behaviors could involve issues such as unauthorized connections or unusual account activity. If you can identify problems early on, you'll have the chance to stop them and mitigate the damage before they turn into something more problematic.
Encrypt Web Traffic
It is also important to encrypt your web traffic. You can do this by investing in an SSL:
SSL stands for Secure Sockets Layer and, in short, it's the standard technology for keeping an internet connection secure and safeguarding any sensitive data that is being sent between two systems, preventing criminals from reading and modifying any information transferred, including potential personal details.
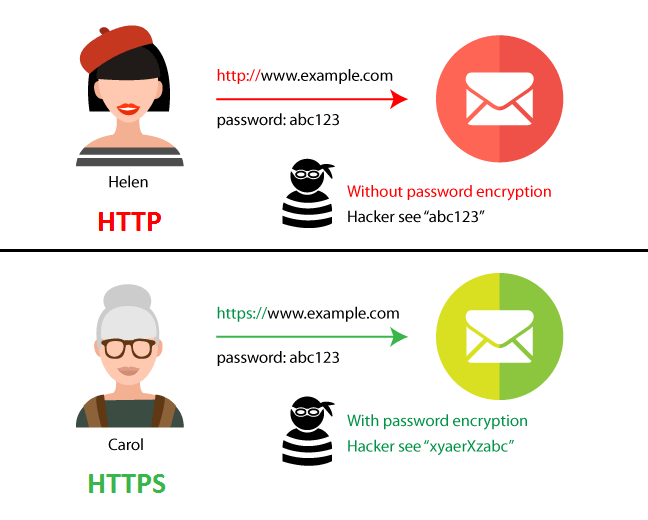
HTTPS, which stands for Hypertext Transfer Protocol Secure, is a more secure version of HTTP:
“The problem with the regular HTTP protocol is that the information that flows from server to browser is not encrypted, which means it can be easily stolen.
HTTPS protocols remedy this by using an SSL certificate, which helps create a secure encrypted connection between the server and the browser, thereby protecting potentially sensitive information from being stolen as its transferred between the server and the browser.”
Besides website security, switching from HTTP to HTTPS is crucial because Google flags every site as unsafe unless it has an HTTPS certification. In August 2014, Google announced that HTTPS is a ranking signal.
Commission Penetration Testing
One of the most effective methods of securing your site is by subjecting it to a penetration test:
Penetration testing (pen testing) is the process of assessing computer systems, networks and applications to identify and address security vulnerabilities that could be exploited by cybercriminals.
These tests look at your website and IT infrastructure and check whether they are vulnerable to the techniques and tactics used by cybercriminals. Organizations can then use the results of the pen test to help them understand where their system needs improving or upgrading.
Before commissioning a pen test, it’s worth undertaking a vulnerability scan to address core vulnerabilities. This enables a pen test to focus on deeper vulnerabilities that automated scanning tools are unable to detect.
Manage User Permissions
Another tip that almost all e-commerce businesses could benefit from is the importance of managing user permissions. You might assume that it is fine to give every member of staff full access to the system so that they can easily get on with their job. But the truth is that most people don’t actually need full access to the system in order to do their work.
If every account has full access, that means that if just one user account is breached, it can allow cybercriminals in to any data that they want. A real-world example of this was the cyber attack on Ticketfly – one webmaster’s account was breached, and because this account had full access to the system, the criminals were able to steal the data of more than 26 million customers.
Conduct Regular Staff Training
It might seem simple, but this last point is something that a huge number of e-commerce organizations overlook:
It is crucial that you provide all your employees with training on basic cybersecurity.
Your staff are a vital line of defense against the actions of cybercriminals, and when they understand not only the kinds of attacks that they are being targeted with, but also the standard steps they should be taking to keep themselves and the business safe, it can make a massive difference.
Don’t assume that a simple training session when they're first hired is enough. Cybercrime is constantly evolving and changing as criminals become more sophisticated. It is important to have regular refresher training sessions with updated material to keep your team prepared.
Conclusion
Every e-commerce business needs to put additional emphasis on keeping their site secure. The increasing sophistication of cybercriminals as well as the availability of tools and information means that businesses of all sizes can be vulnerable to attacks and breaches.
If you run an e-commerce site, you should ensure that you are taking appropriate security measures, as well as investing in training for your staff to reduce the risk of an attack taking place.
More e-commerce content:
- Creating a Winning SEO Strategy for E-commerce Companies
- The 4 Fundamentals of E-commerce Website Design
- How to Set Up Your E-commerce Product Page for Maximum Conversions
- How to Use Content to Boost Your E-Commerce Sales
- Comparison of the Top 6 E-commerce Platforms
The post How to Keep Your E-commerce Site Secure Against Cyber Threats in 2020 appeared first on Single Grain.
from Single Grain https://ift.tt/2NTnkPO

No comments:
Post a Comment